dong
(栋dong)
1
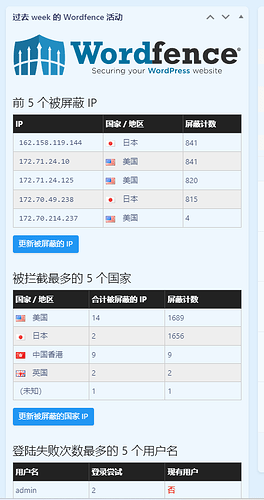
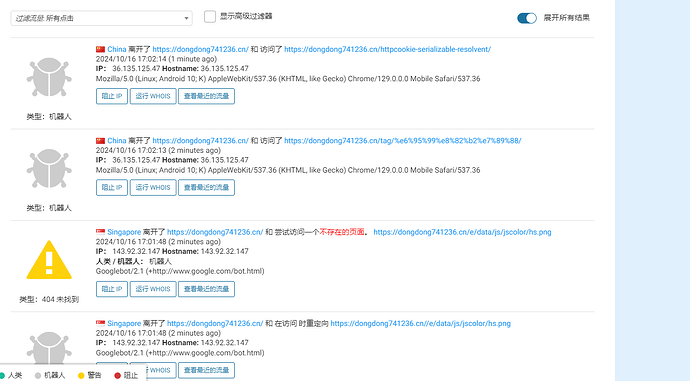
全是cloudflare的ip,我是docker中的wp,然后nginx反向代理,
这是nginx的配置
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name dongdong741236.cn;
index index.php index.html index.htm default.php default.htm default.html;
location / {
proxy_pass http://127.0.0.1:端口;
proxy_redirect off;
# 保证获取到真实IP
proxy_set_header X-Real-IP $remote_addr;
# 真实端口号
proxy_set_header X-Real-Port $remote_port;
# X-Forwarded-For 是一个 HTTP 扩展头部。
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
# 在多级代理的情况下,记录每次代理之前的客户端真实ip
proxy_set_header HTTP_X_FORWARDED_FOR $remote_addr;
# 获取到真实协议
proxy_set_header X-Forwarded-Proto $scheme;
# 真实主机名
proxy_set_header Host $host;
# 设置变量
proxy_set_header X-NginX-Proxy true;
# 开启 brotli
proxy_set_header Accept-Encoding "gzip";
}
# 日志
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
# 证书
ssl_certificate /etc/nginx/ssl/dongdong741236.cn.pem;
ssl_certificate_key /etc/nginx/ssl/dongdong741236.cn.key;
# curl https://ssl-config.mozilla.org/ffdhe2048.txt > /path/to/dhparam
# ssl_dhparam /etc/nginx/ssl/dhparam;
# HSTS (ngx_http_headers_module is required) (63072000 seconds)
add_header Strict-Transport-Security "max-age=63072000" always;
# OCSP stapling
ssl_stapling on;
ssl_stapling_verify on;
# verify chain of trust of OCSP response using Root CA and Intermediate certs
# ssl_trusted_certificate /etc/nginx/ssl/all.sleele.com/fullchain.cer;
# replace with the IP address of your resolver
resolver 223.5.5.5;
resolver_timeout 5s;
}
2 个赞
dong
(栋dong)
5
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name dongdong741236.cn;
index index.php index.html index.htm default.php default.htm default.html;
location / {
proxy_pass http://127.0.0.1:8080;
proxy_redirect off;
# 使用 Cloudflare 的 X-Forwarded-For 来获取真实 IP
real_ip_header X-Forwarded-For;
# 设置信任的 Cloudflare IP 段
set_real_ip_from 103.21.244.0/22;
set_real_ip_from 103.22.200.0/22;
set_real_ip_from 103.31.4.0/22;
set_real_ip_from 104.16.0.0/12;
set_real_ip_from 108.162.192.0/18;
set_real_ip_from 131.0.72.0/22;
set_real_ip_from 141.101.64.0/18;
set_real_ip_from 162.158.0.0/15;
set_real_ip_from 172.64.0.0/13;
set_real_ip_from 173.245.48.0/20;
set_real_ip_from 188.114.96.0/20;
set_real_ip_from 190.93.240.0/20;
set_real_ip_from 197.234.240.0/22;
set_real_ip_from 198.41.128.0/17;
set_real_ip_from 2400:cb00::/32;
set_real_ip_from 2606:4700::/32;
set_real_ip_from 2803:f800::/32;
set_real_ip_from 2405:b500::/32;
set_real_ip_from 2405:8100::/32;
set_real_ip_from 2a06:98c0::/29;
set_real_ip_from 2c0f:f248::/32;
# 保证获取到真实IP
proxy_set_header X-Real-IP $remote_addr;
# 真实端口号
proxy_set_header X-Real-Port $remote_port;
# X-Forwarded-For 是一个 HTTP 扩展头部。
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
# 在多级代理的情况下,记录每次代理之前的客户端真实ip
proxy_set_header HTTP_X_FORWARDED_FOR $remote_addr;
# 获取到真实协议
proxy_set_header X-Forwarded-Proto $scheme;
# 真实主机名
proxy_set_header Host $host;
# 设置变量
proxy_set_header X-NginX-Proxy true;
# 开启 brotli 或 gzip 压缩
proxy_set_header Accept-Encoding "gzip";
}
# 日志
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
# 证书
ssl_certificate /etc/nginx/ssl/dongdong741236.cn.pem;
ssl_certificate_key /etc/nginx/ssl/dongdong741236.cn.key;
# curl https://ssl-config.mozilla.org/ffdhe2048.txt > /path/to/dhparam
# ssl_dhparam /etc/nginx/ssl/dhparam;
# HSTS (63072000 seconds)
add_header Strict-Transport-Security "max-age=63072000" always;
# OCSP stapling
ssl_stapling on;
ssl_stapling_verify on;
# verify chain of trust of OCSP response using Root CA and Intermediate certs
# ssl_trusted_certificate /etc/nginx/ssl/all.sleele.com/fullchain.cer;
# 使用 DNS 解析器(推荐使用 Cloudflare 的 DNS)
resolver 223.5.5.5;
resolver_timeout 5s;
}
这个就好了
1 个赞